The biggest cyber-threat to your law firm is something you use every day – and probably couldn’t live without.
It’s your email.
A whopping 93 percent of cyber breaches are the result of an email phishing attack. And though most people – 78 percent, in fact – know better than to open a suspicious e-message, four percent will click on any given phishing campaign.
Even more disturbing: the more phishing emails someone has opened, the more likely they are to do so again.
These are some of the findings from the 2018 Verizon Data Breach Investigation Report.
Take the Phishing IQ Test
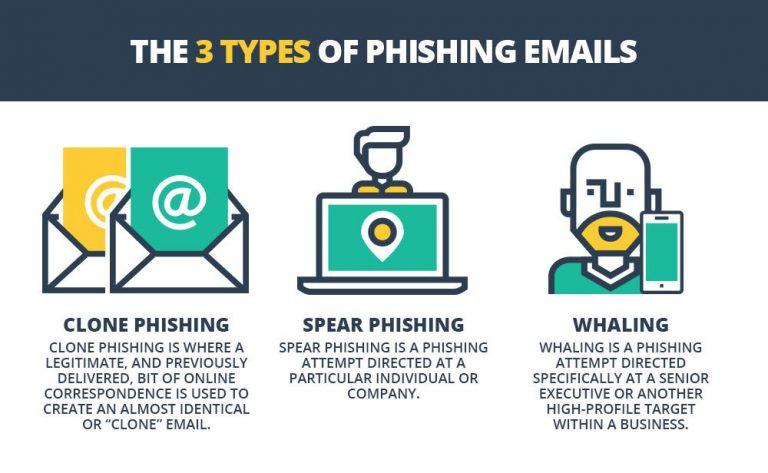
Phishing attacks have become far more sophisticated since the early days of unsolicited emails from the “Nigerian Prince Who Needs Your Help.” The new phishing emails are so good at mimicking actual messages from banks, credit cards and PayPal that it’s hard for even a trained eye to tell the real ones from the fake.
Test your Phishing IQ with this simple quiz.
The 10 question quiz asks you to identify what is an actual email or a phishing email, and it takes only a few minutes. But be forewarned: this is not an easy test. The difficulty in telling the real ones from the fakes illustrates how cyber-vigilance can be a challenge, even for something as simple as email.
Ready? Start your test now.
You’ve Only Got 16 Minutes
What makes the new phishing emails so scary is the lightning speed of their attacks.
From the time you open the email or click on a link, you’ve got exactly16 minutes to take defensive action. After that, it’s probably too late. It takes cyber-crooks only minutes – or even seconds – to do their dirty work. Before you know it, your system has been compromised and your data is being extracted.
And consider this: 68 percent of breaches take months or longer to discover, according to the Verizon Report. Often, it’s not even your office that spots it. It’s a third party such as law enforcement, a vendor, or – worst of all – one of your clients.
9 Tips for Thwarting Cyber Attacks
- Get everyone on board. Make sure every member of your team understands how important cybersecurity is to your brand and bottom line.
- Emphasize cyber education. Discuss spear-phishing and other cyber threats at your next staff meeting. Share common concerns and recurring scenarios. Talk about how to spot warning signs. Even better: bring in an outside security consultant for a training session.
- Have a cyber-security plan. Put it in writing. Even a simple plan covering the basics – such as password protection and phishing awareness – is better than no plan at all. Make compliance with the plan a condition of employment.
- Keep data on a need-to-know basis. Do you know who can see your sensitive data and systems? Limit access to the people who need it to do their jobs. Have procedures to revoke access when they leave your firm or their role changes.
- Patch and update promptly. Cybercriminals know how to exploit known vulnerabilities in your software. Easy safeguards: install patches and keep your anti-virus protection up-to-date.
- Encrypt sensitive data. The odds are that your data will be breached. It might have already happened and you just don’t know it yet. Encrypting your data will render it useless if it is stolen.
- Use two-factor authentication. This will limit the damage if system credentials are lost or stolen.
- Don’t overlook physical security. Not all data theft happens online. Surveillance cameras and entry access for restricted areas can help prevent criminals from tampering with systems or stealing sensitive material. An office policy that covers the use of laptops and portable devices off-site can reduce the risk of inadvertent disclosure.
- Purchase cyber-liability insurance coverage. A cyber policy is a firewall against hackers, data theft and system breaches.
Want to learn more ways to improve your firm’s cyber-security? Check out the Technology and Security section of our Pro Practice Resource Center.
Sources:
- 2018 Verizon Data Breach Investigation Report https://enterprise.verizon.com/resources/reports/DBIR_2018_Report_execsummary.pdf
- Phishing Box https://www.phishingbox.com/